
繁體中文 | English


CSK (Crystal Security Keeper) is a solution to automate information security management and compliance security control. CSK provides program translation and dynamic detection to implement enterprises’ information security regulations into end-user’s platform as well as regularly manage risks through automatic auditing. CSK’s security baseline can be defined accordingly with corporate demands, while the status of corporate information security compliance can be monitored through mechanisms including association analysis, configuration profiling and dynamically audited content analysis, resulting quantitative risk assessment as well as reliable reports for continuous information security management and enforcement.
CSK covers critical technology such as safety detection (information detection, vulnerability scanning, security updates), configuration security control, compliance and risk management. Different from traditional detection defense, CSK brings information security protection into a new phase of prevention before hand and provides a comprehensive solution of automated information security governance for corporate organizations.
 |
Installation Requirements for CSK Controller
Opration System :Win XP,Win Vista,Win 7,Win Server 2000 and 2008 Database : MySQL 5.5+ JRE : JRE 6+ |
 |
Installation Requirements for CSK Agent Green Software and no need to install,and support agent trigger scan. Opration System :Win XP,Win Vista,Win 7,Win Server 2000 and 2008 |
 |
CSK Solutions Baseline Support :USGCB(FDCC),MS-SCM Baselines(keep updating) Audit Coverage :Win XP,Vista,Win 7,Win Server 2000 and 2008,Win XP and Vista Firewall Audit Contents :System Configuration,OS/App vulnerabilities,OS and software Path,software authentication (keep updating) Scores for all vulnerabilities :CVSS(Common Vulnerability Scoring System ) |
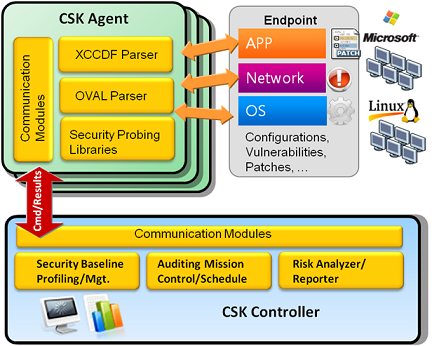
CSK software includes two major parts: CSK Controller information security governance service platform, as well as CSK Agent information security terminal auditing software.
CSK Controller :It provides functions such as information security policy editing, auditing mission management, association analysis of detection baseline, detection result analysis, risk quantitative analysis, and quantitative indicator management. The CSK Controller saves information like security management policy, systematic setting inspection, software status profile and auditing results, besides, it associates with complicated detection rules and standards to evaluate threats, manage auditing process and tracking.
CSK Agent :The CSK Agent is a green software which requires no installation and is able to operate directly on terminals to detect configuration setting, vulnerable leakage, patching work and security updates. Based on security standards detection specified by CSK Controller, the Agent can detect OS on various terminals, network services and application’s security status and report to CSK Controller to conduct further risk analysis.
Complete informational security check procedure
CSK provides complete and flexible detection procedure. It can do compliance check according to each endpoint’s status of system security, configuration security, software weakness and security updates. The results can be compared to international information security standard database such as CCE, CPE and OVAL, through scheduling support to real-time and regular check to provide complete results and detailed report to the administrator as aids and reference to grasp corporate information security policy implementation as well as strengthen informational security control.
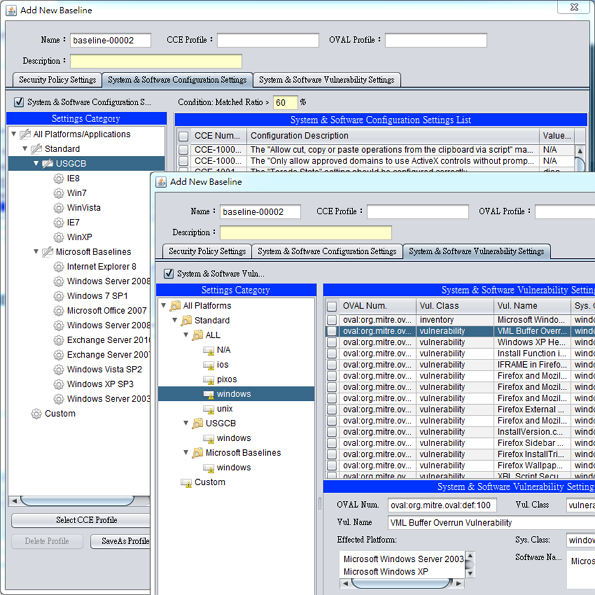 Complete security baseline management
CSK’s security baseline setting supports protocols defined by National Checklist Program Repository (NCP), in addition to USGCB and Microsoft’s information security baseline for terminals, CSK’s built in information security association matrix can produce compliance check reports which comply with ISO 27001, NIST SP800 or PCI DSS. Users can also modify different information security management specification according to demands of various application arena such as finance and healthcare.
System software configuration security check
Information security standard setting includes specifications of system security, configuration setting, software weakness, and security updates. The configuration setting, in particular, follows syntax of XCCDF(The Extensible Configuration Checklist Description Format) while integrates standard libraries such as CPE(Common Platform Enumeration), and CCE(Common Configuration Enumeration) to provide consistent information expression that connects other services to strengthen information security governance.
Systematic software weakness check
With regard to software vulnerability compliance check, CSK develop Agent based check through automatic deciphering and OVAL (Open Vulnerability Assessment Language) to enlarge scope of software weakness check to cover non-network service terminals as well as systematic weakness scan, and avoid false-positive or false-negative problems occurring in traditional weakness scan. In addition to customized system security standard, CSK provides users customized baseline profiles for configuration and software weakness compliance check. The security standard also offers exporting and importing functions for different units to conduct identical check standard evaluation.
Complete security baseline management
CSK’s security baseline setting supports protocols defined by National Checklist Program Repository (NCP), in addition to USGCB and Microsoft’s information security baseline for terminals, CSK’s built in information security association matrix can produce compliance check reports which comply with ISO 27001, NIST SP800 or PCI DSS. Users can also modify different information security management specification according to demands of various application arena such as finance and healthcare.
System software configuration security check
Information security standard setting includes specifications of system security, configuration setting, software weakness, and security updates. The configuration setting, in particular, follows syntax of XCCDF(The Extensible Configuration Checklist Description Format) while integrates standard libraries such as CPE(Common Platform Enumeration), and CCE(Common Configuration Enumeration) to provide consistent information expression that connects other services to strengthen information security governance.
Systematic software weakness check
With regard to software vulnerability compliance check, CSK develop Agent based check through automatic deciphering and OVAL (Open Vulnerability Assessment Language) to enlarge scope of software weakness check to cover non-network service terminals as well as systematic weakness scan, and avoid false-positive or false-negative problems occurring in traditional weakness scan. In addition to customized system security standard, CSK provides users customized baseline profiles for configuration and software weakness compliance check. The security standard also offers exporting and importing functions for different units to conduct identical check standard evaluation.
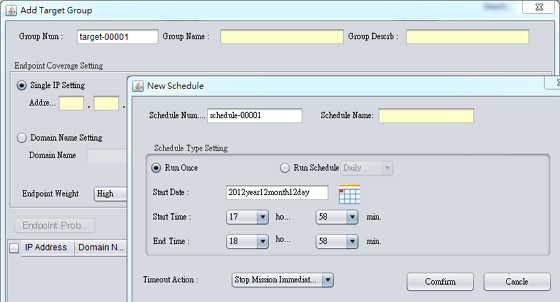
Flexible check target and scheduling control
Corporate informational security auditors can set up check target with flexibility in single IP, specific address range, or importing terminal system checklist in accordance with different terminal device setting, computer types (general user or server)
Meanwhile, to help auditing personnel better grasp CSK Agent’s deploying status before official auditing check, it enables checking groups to conduct terminal data collection and deployment detection on target management page. And as a result, corporate information security auditors can select applicable security baseline according to terminal association analysis to enhance efficiency through decreasing processed data.
CSK also provides scheduling function for different checking mission. In addition to immediately executing checks, auditors are able to set appropriate checking point periodically to provide flexible and efficient check and auditing control. Moreover, CSK is able to execute automatic double scan for terminals failed to scan in the first place to strengthen the completion of checking mission execution.
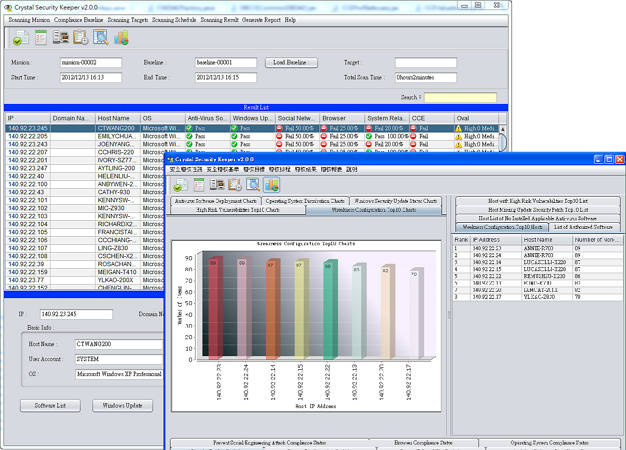 Real-time result check and tracking
The result of every checking mission can be imported with scanned time point accordingly while corporate information security auditors are able to dynamically select security baseline in comparison with results. Each terminal check result includes installed software license, OS security updates, system’s security settings, software weakness, risk assessment (in accordance with CVSS 2.0 assessment standard) and security protection status for every computer. It can also modify standards or strengthen security control mechanism according to compliance status.
Real-time result check and tracking
The result of every checking mission can be imported with scanned time point accordingly while corporate information security auditors are able to dynamically select security baseline in comparison with results. Each terminal check result includes installed software license, OS security updates, system’s security settings, software weakness, risk assessment (in accordance with CVSS 2.0 assessment standard) and security protection status for every computer. It can also modify standards or strengthen security control mechanism according to compliance status.
In addition to check result and checklist, CSK Controller analyze statistics regarding each compliance baseline and present the data in ranking and diagram such as Top 10 incompliant configuration, Top 10 high-risk weakness, not-yet-installed security updates, and system protection status statistics.
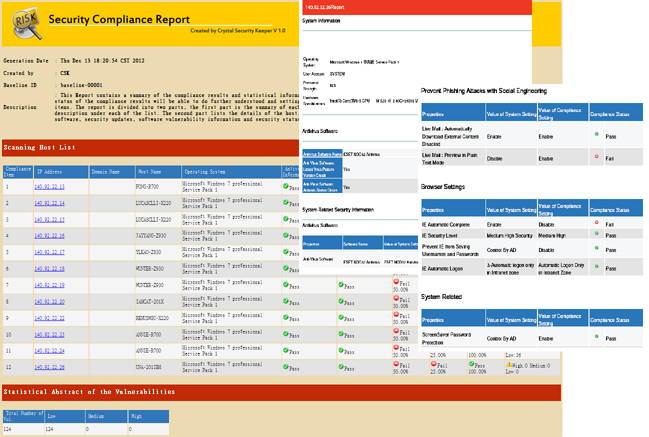
Check result compliance report
CSK Controller can produce complete report in accordance with checking mission and association information security baseline. Reports including information format in diagram, ranking and statistics can be exported to PDF and HTML format for management reference. In addition to comprehensive analysis reports, CSK provides individual reports for host under test to help users examine own devices’ information security compliance status and reinforce security.
Besides, CSK is able to present test results according to ISO 27001 to examine information security policy implementation in each control fields. Moreover, CSK support directly use XML format to record test result and offer import/export functions as well as integrated multiple results. While applying into large business organizations, CSK system is able to test and assimilate results via multiple distributed CSK controllers, allowing information governance to be independent of time and space constraints.
Flexible and automatic updating mechanism
CSK Controller is equipped with built-in Update Server. While updating security baseline and databases like XCCDF, OVAL, CCE and CVE database, CSK automatically synchronizes checking mechanism and updates. In the mean time, CSK Agent can set automatic updates checking frequency and host information, updating mechanism mentioned above can automatically update all CSK Agent software deployed in corporate organization.
In addition to cooperating with international information security experts, the CyberTrust Technology Institute (CTTI)at Institute for Information Technology (III)has professional information security R&D team to analyze latest Internet attack trend and cases, as well as research on checking methods to shorten threat existing time and provide CSK reliable checking capability such as XCCDF, OVAL checking module updates, international information security baseline expansion, and strengthening relevant functions.





